When your imported certificate chain does not match the one on LDAPS you wont be able to connect by encrypted connection.
As a workaround you could use HAProxy since it let’s you disable certificate chain verification. Please don’t use this in mission critical networks since an attacker could use this as a MITM target.
Install HAProxy the usual way and do the following:
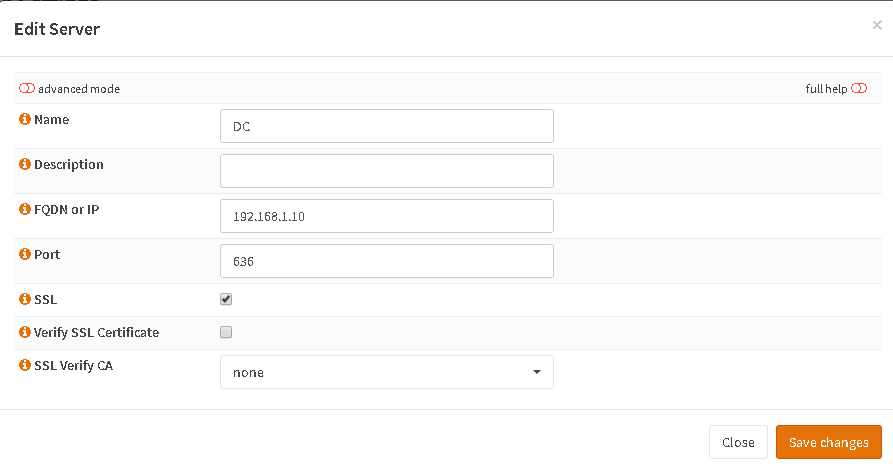
Create a Real Server
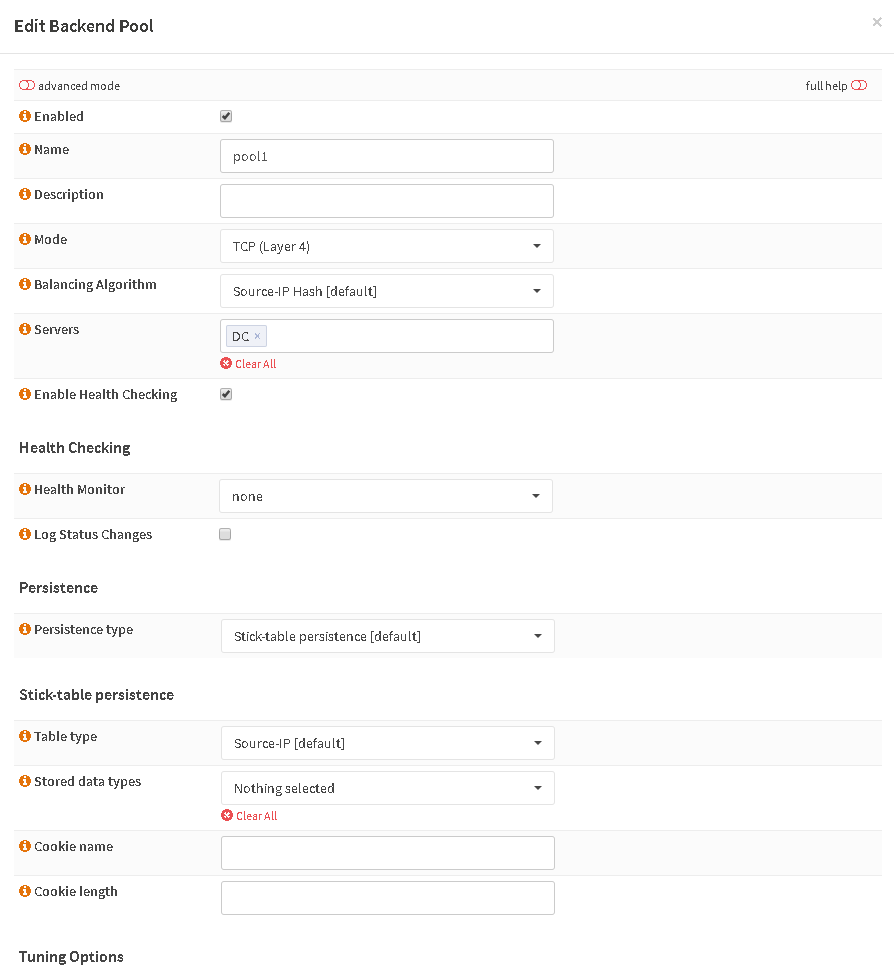
Create a Backend Pool
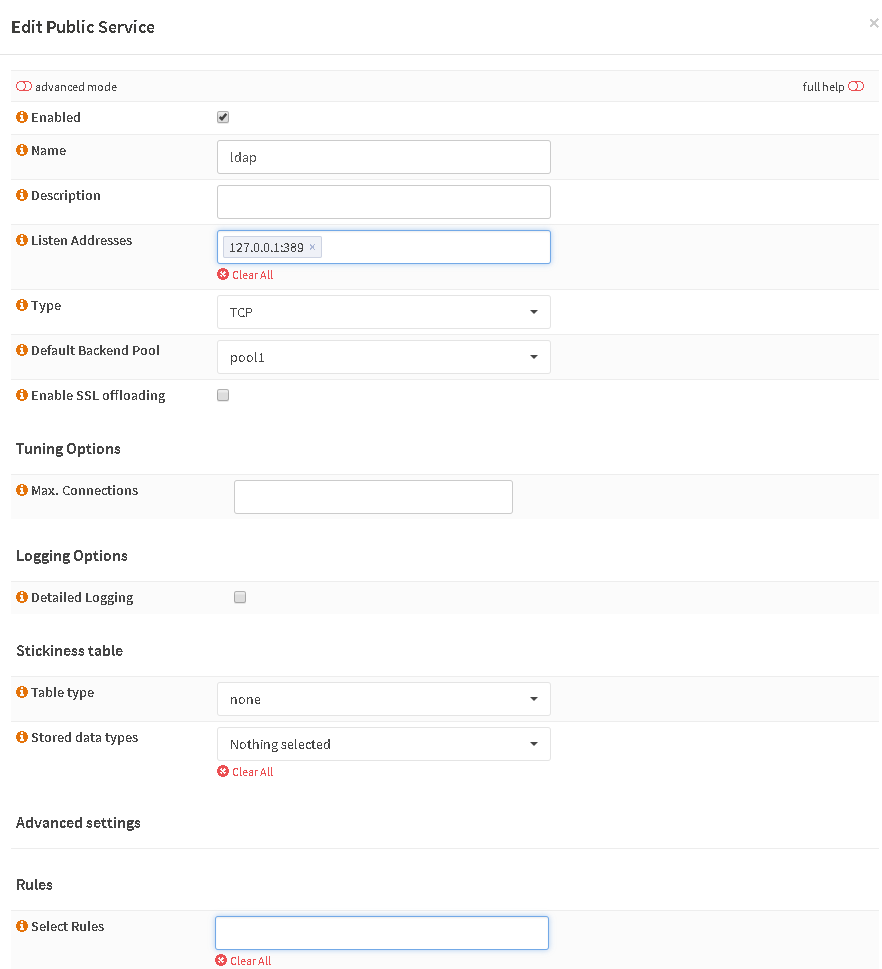
Create a Public Service
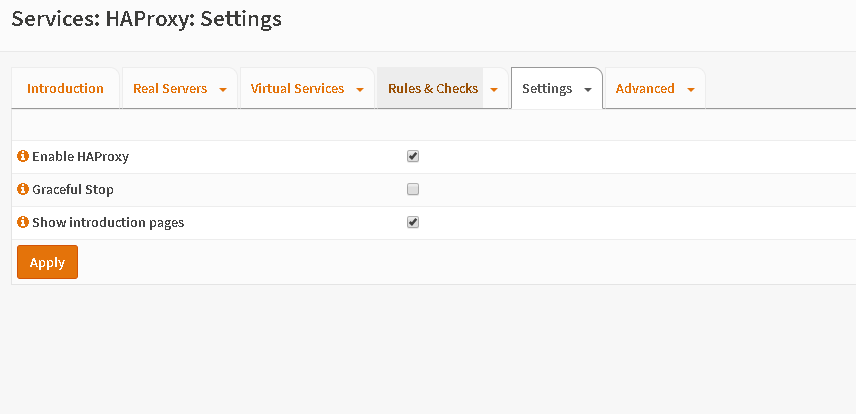
Finally Enable the service.
Now you can create a new LDAP backend and point it to localhost 389, it will be forwarded to your DC with LDAPS (636)