Intro
Short installation and configuration instructions for WireGuard Plugin 0.3 devel with AzireVPN (see also notes at the end).
Installation
Installation in devel mode only works via CLI:
# opnsense-code plugins
# cd /usr/plugins/net/wireguard
# make upgrade
Then you’ll see the menu under VPN – WireGuard
Setup
Login into your Azire account and request a config for WireGuard.
Go to tab Endpoints, add a new one and fill out the public key from the config file, Tunnel Address as 0.0.0.0/0 and the VPN host in Endpoint Address
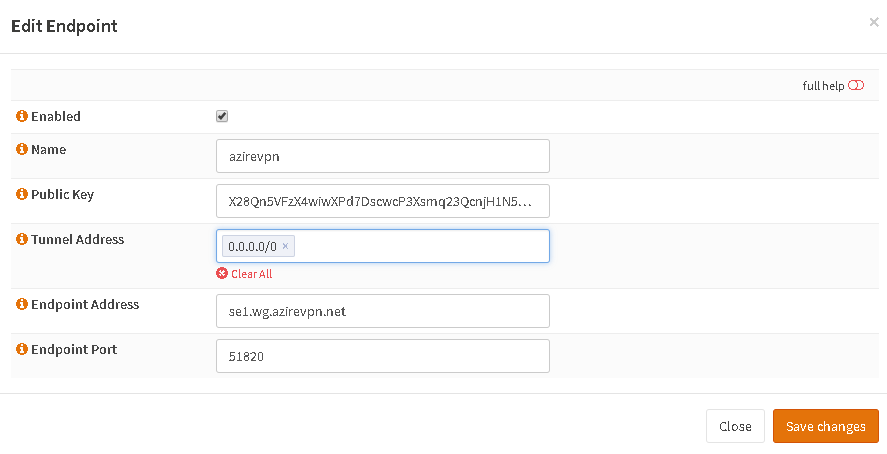
Normally the creation of a new server instance would create a new keypair. Since the keys with Azire are managed by them you have to include the private key from the text file you downloaded and set as Tunnel Address the one in the config
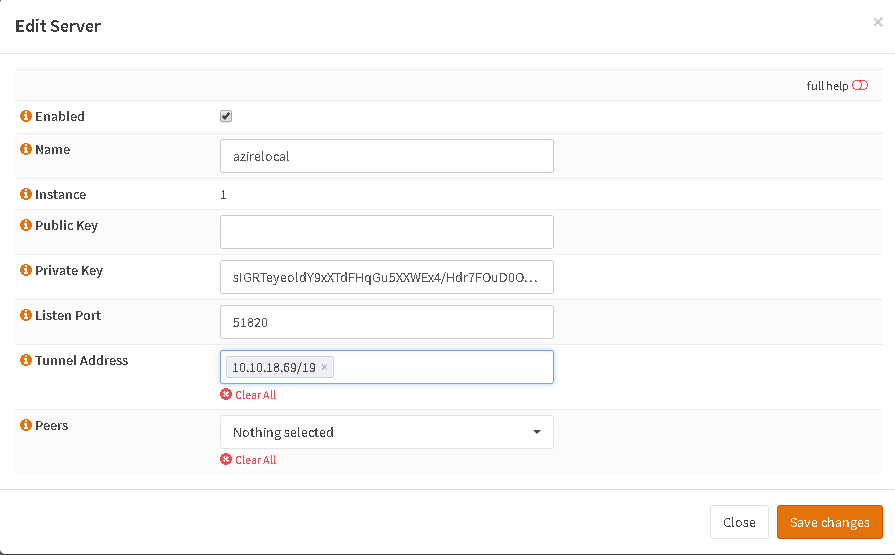
Choose your Endpoint in the dropdown list of Peers.
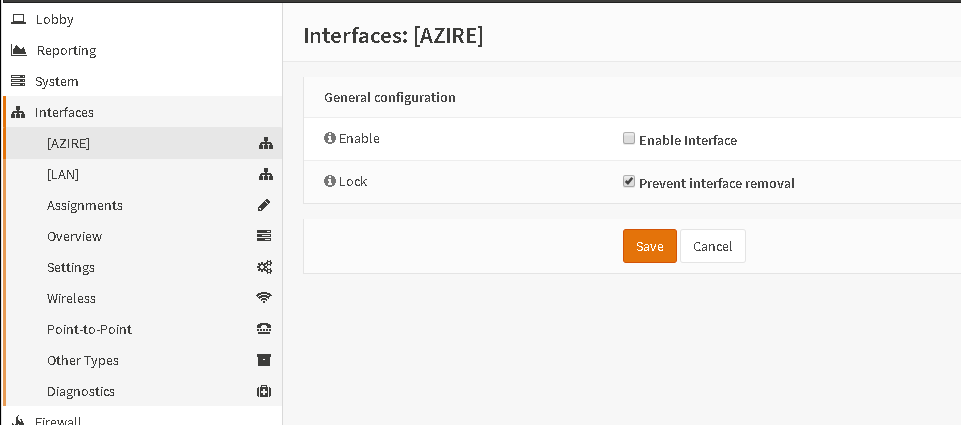
Then go to tab General and enable the service. If everything is well the tunnel is up and your default is now via WireGuard. To make more out of it, go to Interfaces – Asssignments and assign your wg0 interface.
IMPORTANT: Never enable this interface!! Just tick the lock to prevent interface remove. You can enable, rename the interface and disable again so it’s name is not just optX.
Now you can enable the Interfae and set IPv4 to none
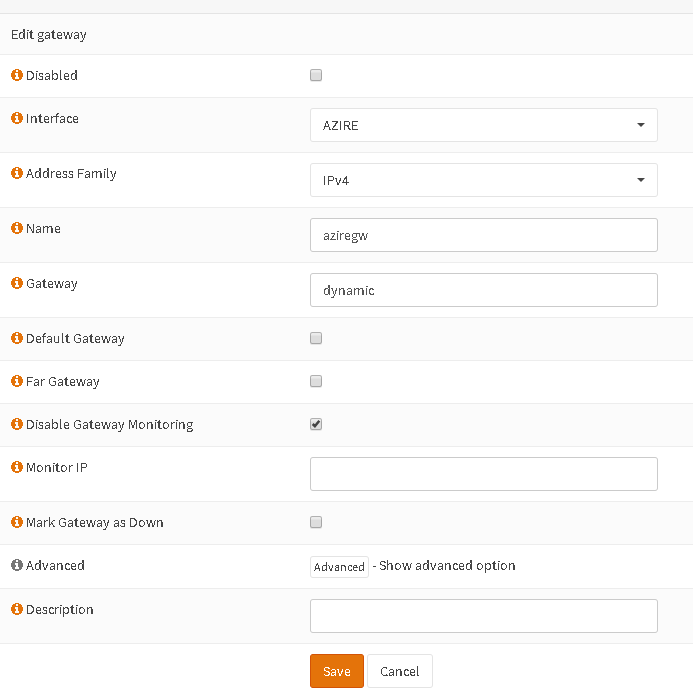
After this you can create a gateway in order to set route via Firewall rules
Now you can set a Firewall rule and push your LAN of whatever through it:
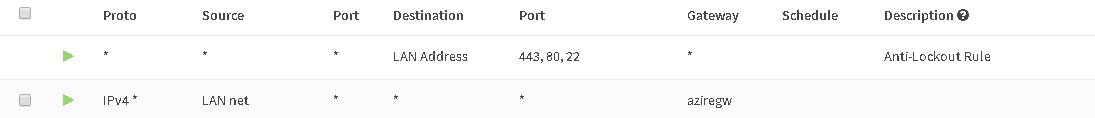
So, now you push all you LAN via the tunnel, what’s missing is a NAT rule so you are nattet in the tunnel. Go to Firewall – NAT – Outbound and set to Hybrid or Manual. Then add a rule like below and choose your assigned IP from the config file:
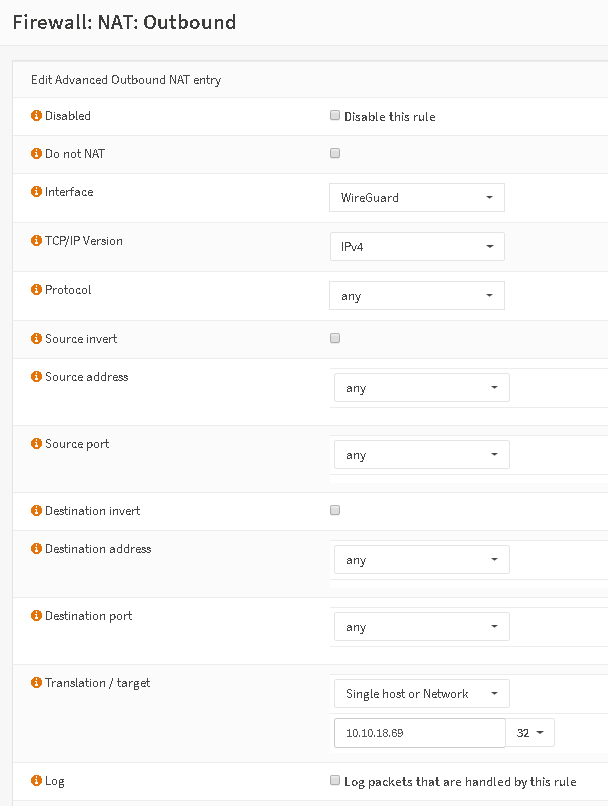
That’s it!
If you have questions ping me (mimugmail) in IRC, OPNsense Forums or Reddit. Also available in Twitter (mimu_muc) to help out!
P.S.: Perhaps you have to restart the service since the assignment of the interface without IPv4 removes the current setup.
P.P.S.: ATM the routing via groups doesn’t work when the interface is disabled, we’ll have to fix this in core (may take some weeks). For now you can just use the routing received via the server instance (like 0.0.0.0/0).