Update:
If you are new to OPNsense please use Option 0 in this guide:
https://www.routerperformance.net/opnsense/using-pfblocker-features-in-opnsense/
Intro
Via BIND Plugin introduced in 18.7 you can use DNSBL via RPZ like with PiHole or pfBlockerNG.
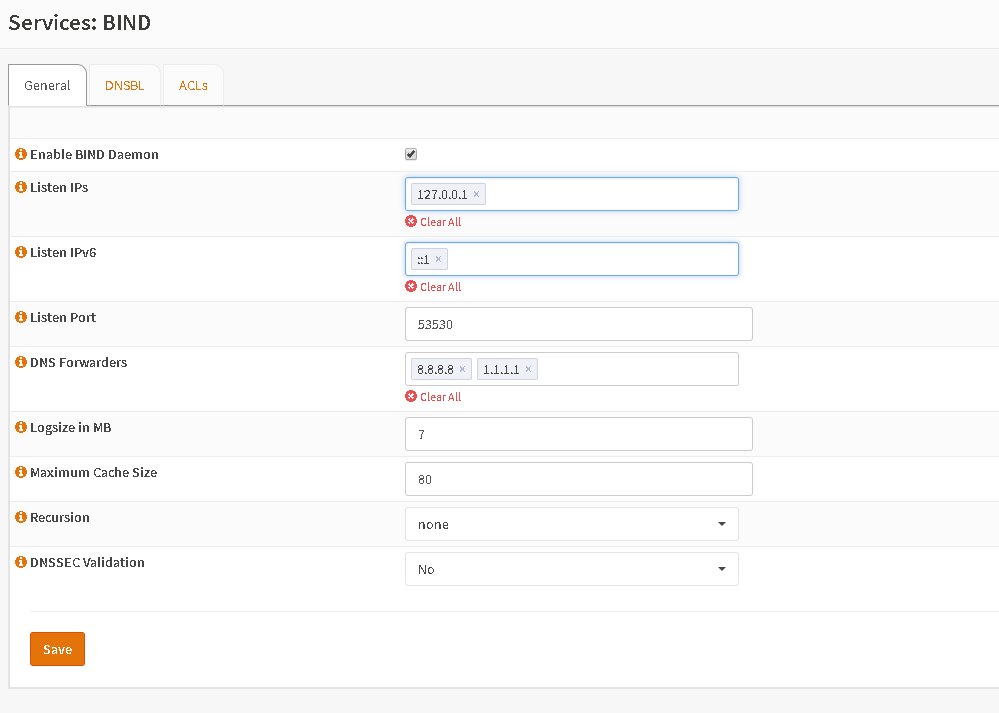
In the default install the service listens only on localhost and port 53530 to not interfere with current setups of Unbound, dnsmasq or mdns.
Setup Plugin
First enable the plugin and set forwarders if you like (e.g. 8.8.8.8 or 1.1.1.1). If you don’t set forwarders BIND will try to resolve directly with the root name servers. The rest of the page is perfectly fine as a default.
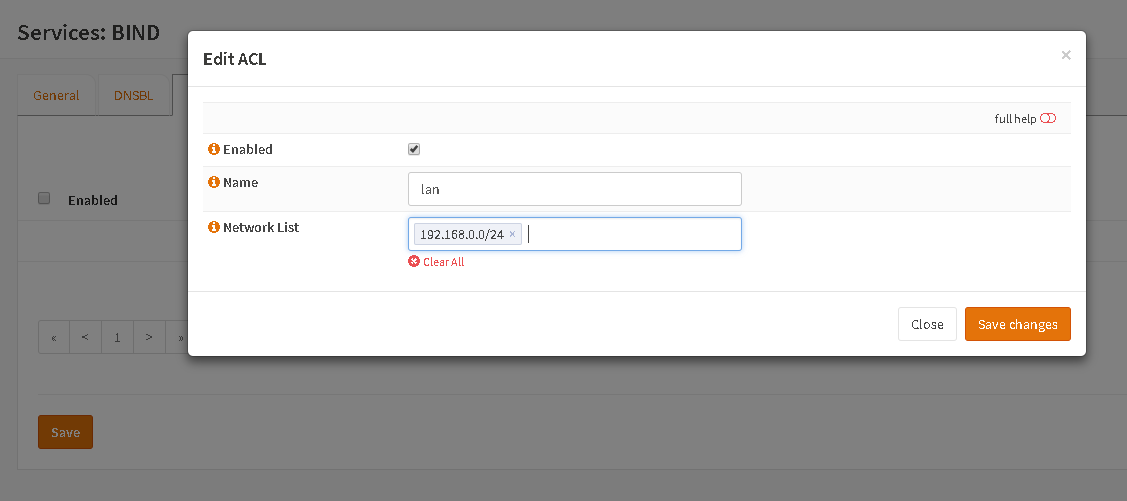
Go to ACLs and set up an access-list with your private LAN:
Hit „Save changes“ and „Save“ and go back to „General“ where you can choose the ACL under „Recursion“. Hit „Save“ again and now you LAN is allowed to do recursion via the plugin.
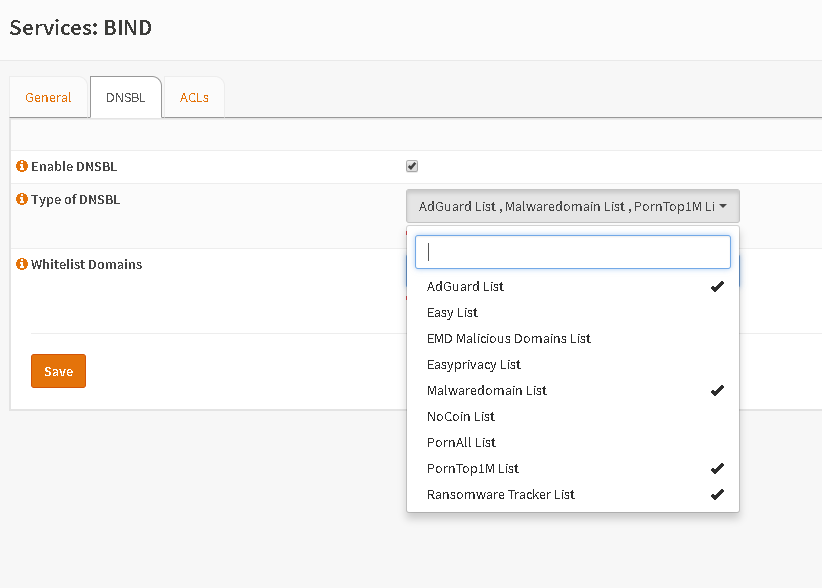
Now go to tab „DNSBL“ and set the lists you like. After hitting „Save“ it could take some time for downloading.
Via „Whitelist Domains“ you can add some exclusions if you found some.
Setup Firewall
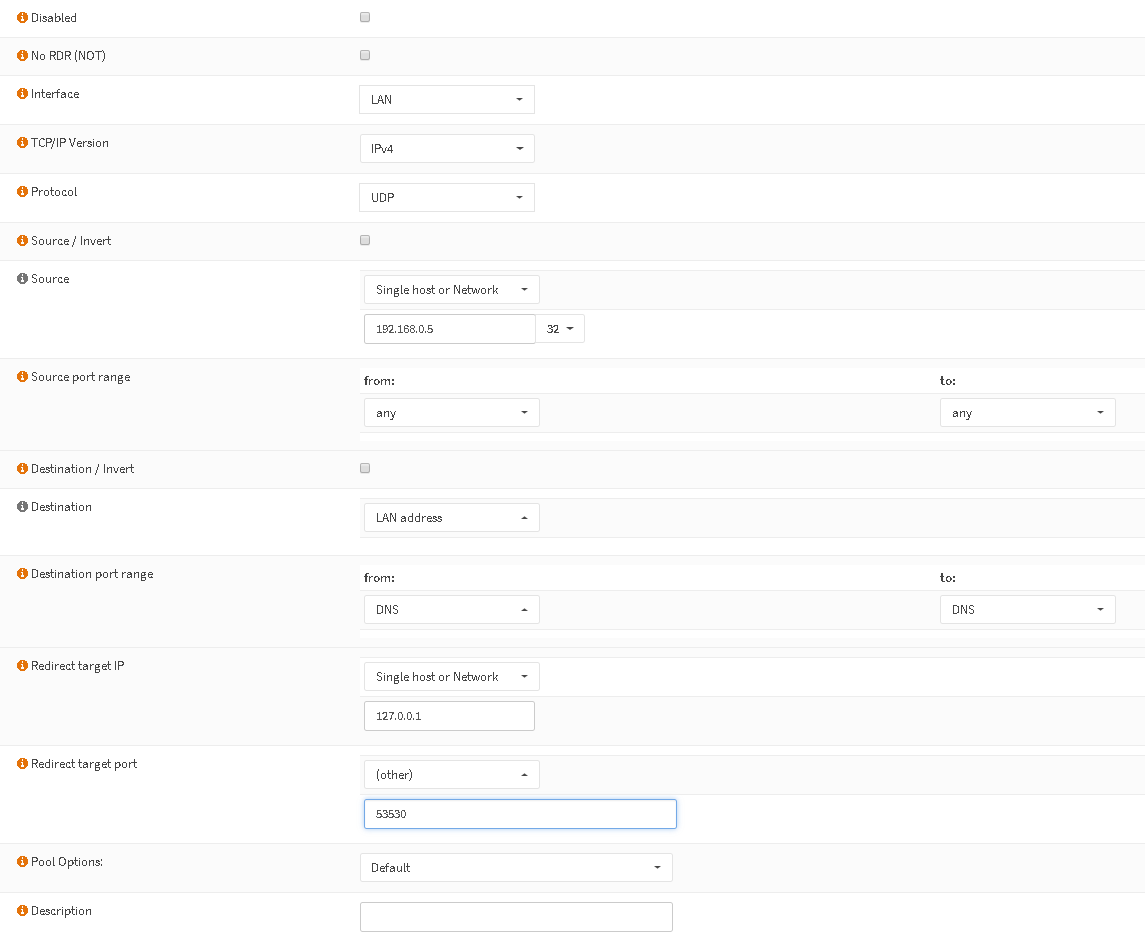
Now every DNS request reaching localhost:53530 will checked against your blacklists. Since you’ll surely have a running setup of Unbound or dnsmasq, we could first try with a portforward to redirect some clients to our instance directly. The advantage is that you can select a list for IPs to check against DNSBL but not every client. Perhaps some members of the family want to reach specific sites 🙂
The following would only redirect IP 192.168.0.5 to your BIND instance:
If it runs fine for you, you could change „Source“ to „LAN net“.
Fixed Unbound Config
When you think your setup runs stable and you still need your Unbound cause of local overrides you can set BIND as your forwarder in Unbound. Just add this to yout custom options field:
do-not-query-localhost: no
forward-zone:
name: „.“
forward-addr: 127.0.0.1@53530